 |

|

|
||||||
 |
||||||
by A. K. Dewdney
Further, the process of transformation, even if it brings revolutionary change, is likely to be a long one, absent some catastrophic and catalyzing event – like a new Pearl Harbor.
from Rebuilding America’s Defenses, Project for a New American Century September, 2000
1. Introduction
Every forensic investigation of sufficient magnitude and importance relies on two main elements, in general: analysis of evidence and scenario construction. Let us say that a crime has been committed and that a suspect in the crime has explained the superficial facts of the case in terms of a scenario, a story that, if shown to be consistent with the facts, allows the suspect freedom from further suspicion. If the investigators discover facts that are inconsistent with the suspect’s story, however, he is in trouble. The investigators, meanwhile, may also have constructed another scenario in which the suspect plays a key role, one that would incriminate him.
The two elements of the investigation are therefore the analysis of evidence and the construction of scenarios that are consistent with the evidence. It must be pointed out, however, that contradictions in the evidence would warrant holding the prisoner or, if the suspect were still at large, finding and arresting him.
The 9/11 scenario suggested by the Bush administration involved 19 Arab hijackers taking over four passenger aircraft and attempting to fly them into public landmarks of America, a blow to national pride and a surefire stick in the hornets’ nest. According to the official scenario, they succeeded in three of the four attempts.
The 9/11 Commission, which was to check this scenario against the facts on the ground, failed to consider any of the multiple inconsistencies in the official story, not to mention direct and serious contradictions with scientific and technical findings of other groups of concerned citizens, some well supplied with all the needed scientific, technical, and other professional expertise required to check the Bush scenario. (PQ9 2007)
Hitherto lacking has been a comprehensive account of what may really have happened that day. A few attempts have been made in this direction (Spencer 2003), (FME 2005), but they tend to be short and somewhat sparse. Presently, the collective account is fragmentary, with different investigators and investigative groups contributing different pieces of the puzzle, some minor, some major. The pieces are there now, many fitting in just one way. Other pieces of the puzzle are still missing and, in such cases, we may entertain more than one possibility. The resulting picture is called Operation Pearl.
The author has been involved in both aspects of the investigation at hand. Having discovered what did not happen that day, I have been naturally curious about what did happen. This scenario replaces the previous one of the same name. (Dewdney 2006)
The previous version of Operation Pearl took account of all the major pieces of evidence that were inconsistent with the official story (which can now safely be called a public myth). But it failed to recognize the crucial role played by the war games exercises taking place on the morning of 9/11, even before the first aircraft struck the north tower of the world Trade Center (WTC). This has enabled us to move some aspects of the previous scenario to a firmer and more realistic footing — not to mention simplifying them.
The twofold aspect of a criminal investigation described above is one that we urge readers to remember: you must erect a mental firewall in your mind. The firewall separates what did not happen from what did happen. By far the most important investigation is in the first category. This involves the analysis of evidence gleaned from reliable sources, most of them official. It can now be said, for example, that the World Trade Center buildings did not collapse as the direct or indirect result of fires caused by the impacts of aircraft. It can now be said that the official story fails to be supported by the evidence. The official story is wrong — apparently a deliberate falsehood and certainly deserving of its new name on the web: The Official Conspiracy Theory or OCT.
1.1 What is a Theory?
Investigative findings in the what did not happen category involve no “theories†whatever, but result from the application of well-known physical facts and principles to the evidence at hand. In the particular case just mentioned, the analyses were carried out by experienced and knowledgeable physicists and other
experts and made available through a number of key websites. It is a simple physical fact that jet fuel (kerosene) could burn all day against the massive internal support columns of the WTC towers without even weakening them significantly. (Mitchell 2007) We do not need to use the fact that the kerosene fires burned for less than 10 minutes (NIST 2005), or that the few fires remaining in the building were mostly oxygen-starved, low-temperature office fires. Nor do we need the taped communications with the fire director on the affected floors stating that the situation was under control and that evacuation was proceeding in orderly fashion. (The office workers were not being cooked.) Nor do we need the videotaped admission by the WTC leaseholder that WTC Building 7 (which was not struck by a aircraft) had been brought down by controlled demolition. Nor do we need the authoritative refutation by experts of the poorly developed “pancake theory.†(Griffin 2007) We only need the physical facts and principles coupled with readily verifiable information and data freely available from “official†sources.
The buildings did not collapse as the result of the fires. To say what did happen, however, is somewhat more difficult, at least if one wants all the details of how the buildings were brought down. At the most general level one can safely say that some form of controlled demolition was used. It did not involve the same kind of cutting charges, but more powerful explosives. There is abundant evidence, both macro and micro, that cutting charges were used. At the macro level there are photographs of steel support columns with typical diagonal cuts to promote collapse; melted steel decorates the cuts. At the micro level, a substance known as nano-thermite has been found in all samples of the dust from the WTC explosions. The finding was made by American physicist Stephen Jones and later confirmed by Danish physicist, Niels Harrit. (See articles on this site) Both scientists used a scanning electron microscope (SEM) to detect the indelible signature of nanothermite, with precisely the right ingredients, a mechanical mixture of powdered iron, aluminum and sulfur). Suitably confined, nanothermite can also act as a high explosive.
Suffice it to say that such a demolition, even should it prove to contain a number of exotic elements, is entirely within human capability and requires very little further elaboration to be taken as the only realistic scenario. In the larger context of 9/11 we may use the word “theory†in the technical sense of a criminal investigation. Although detectives sometimes investigate “conspiracies†(e.g. conspiracy to defraud or conspiracy to commit murder) the theory, per se, is not about any conspiracy. It’s simply an attempt to piece together what really
happened, a scenario.
The idea of a conspiracy only comes into play when one asks, “whodunit?†Our only observation in this area requires very little reflection. If Arab hijackers didn’t do it, someone else must have. The size of the operation would dictate many operatives working in secret to make it look like an attack by Al Qaeda (or whomever) and, yes, most people would call that a “conspiracyâ€, although in the context of involvement by the spy agencies of various countries, it would be more accurate to call it an “operationâ€. To find out who was really behind the events of that day is not our present business and we are under no obligation to do so.
The present scenario therefore amounts to an existence proof at the most basic level. In other words, a feasible alternative does exist. As such, it also serves to answer a question frequently asked by visitors to Physics 9/11 and similar websites: “If X didn’t happen the way they say it did, how else could it have happened?†The operative word here is “could.†A feasible scenario can answer that question, as well. The scenario constructed in this article also serves as an example of what the intelligence community calls a “false flag†operation, albeit more elaborate than most such operations. Controlled demolitions (of the normal variety) are everyday news, so no one has to strain their imaginations to grasp the basic concept. But false flag operations are never in the news, so the concept must be explained in the context of the events of September 11, 2001.
1.2 Operation Northwoods
Many people boggle at the idea that their own government could cooperate in such a scheme. But a plan by the Joint Chiefs in the early 1960s to launch a false flag attack on the United States (blaming Cuba) is relatively well known, at least to people who follow intelligence and security affairs. The Joint Chiefs considered a number of false flag operations, elaborating plans to ". . . create an incident which will demonstrate convincingly that a Cuban aircraft has attacked and shot down a chartered civil airliner en route from the United States to Jamaica, Guatemala, Panama or Venezuela. The destination would be chosen so that the aircraft would overfly Cuba. The passengers could be a group of college students off on a holiday or any grouping of persons with a common interest to support chartering a nonscheduled flight."
General Lemnitzer and the Joint Chiefs worked out a complex deception to bring this plan to life: An aircraft at Elgin AFB would be painted and numbered as the exact duplicate of a passenger aircraft flying out of Miami. The latter would be boarded by selected passengers having carefully prepared aliases. The former would operate as a drone, or remotely controlled aircraft. At a designated time during their flights, the duplicate would be substituted for the actual civil aircraft at a rendezvous point south of Florida.
From the rendezvous point the passenger-carrying aircraft would descend to minimum altitude and go directly into an auxiliary field at Elgin AFB where arrangements would be in place to evacuate the passengers and return the aircraft to its original state. The drone aircraft, meanwhile, would take off and continue to fly the planned route over Cuba. Once in Cuban airspace the drone would transmit a "May Day" message stating that it was under attack by a Cuban MiG aircraft. The transmission would be interrupted by destruction of the aircraft, when explosives planted on board would be triggered remotely. The transmission would be picked up by ICAO (International Civil Aviation Organization) radio stations in the Western Hemisphere and the information relayed to all concerned authorities. The media could be depended upon to trumpet the news, creating fear and anger in the populace and thus giving the military a free hand to attack Cuba. (Bamford 2001)
The fact that the Joint Chiefs considered such a plan in the early 1960s does not necessarily mean that the Joint Chiefs devised Operation Pearl. It only means that, at the highest levels in the command structure of the US military, such ideas have been introduced before and have found a degree of acceptance.
1.3 Operation Gladio
Operation Gladio is an undisputed historical fact. Gladio was part of a post-World War II program set up by the CIA and NATO supposedly to thwart future Soviet/communist invasions or influence in Italy and Western Europe. In fact, it became a state-sponsored right-wing terrorist network, involved in false flag operations and the subversion of democracy.
The existence of Gladio was confirmed and admitted by the Italian government in 1990, after a judge, Felice Casson, discovered the network in the course of his investigations into right-wing terrorism. Italian prime minister Giulio Andreotti admitted Gladio’s existence but tried to minimize its significance.
The main function of the Gladio-style groups, in the absence of Soviet invasion,
seems to have been to discredit left-wing groups and politicians through the use of “the strategy of tension,†including false-flag terrorism. The strategy of tension is a concept for control and manipulation of public opinion through the use of fear, propaganda, agents provacateurs, terrorism, etc. The aim was to instill fear into the populace while framing communist and left-wing political opponents for terrorist atrocities.
For example, the August 2, 1980 bombing of the Bologna train station which killed 85 people, is widely recognized as a Gladio operation. While it was initially blamed on the communist “Red Brigades,†eventually, right-wing and fascist elements were discovered to be the culprits. Two Italian secret service agents and Licio Gelli, head of the infamous P2 Masonic lodge, were convicted in connection with the bombing.
According to a recent summary of the operation (Ganser 2007) the following countries turned out to have Gladio networks operating in them. Not all countries suffered from the synthetic terrorism, but for the ones that did, an example is provided for each.
| Country | Group Code Name(s) | |
| Italy | Gladio | |
| Turkey | Counter-Guerilla | |
| Spain | CESID | |
| Portugal | Aginter Press | |
| Greece | LOK | |
| France | Plan Bleu | |
| Germany | TD BDJ | |
| Austria | OWSGV | |
| Switzerland | P26 | |
| Belgium | SDRA8 STC | |
| Netherlands | Group O, Group I | |
| Denmark | Absalon | |
| Norway | ROC | |
| Sweden | Unknown | |
| Finland | Unknown |
The synthetic terror operations extended over two decades. One of the infamous early operations was the 1969 Piazza Fontana bombing in Milan that killed 16 people, and injured another 80. General Giandelio Maletti, former head of Italian counterintelligence, claimed the attack was a Gladio operation.
Among the operations attributed to the Gladio are a coup d’etat in Greece in 1967 (LOK), the Frankfurt department store bombing of 1968 (TD BDJ), the Talksim Square massacre in Turkey in 1977 (Counter-guerilla), the Bologna Train Station bombing of 1980 (Gladio), the Brabant Massacres in Belgium from 1983 to 1985 (SDRA8 STC), the assassination of Swedish Prime Minister Olaf Palme in 1986, and — even farther afield — massacres in Guatemala attributed to the Aginter Press group.
As far as is known, all attacks attributed to the Red Brigades, Bader Meinhof or other “terrorist†organizations during the period in question were in fact the work of Gladio cells of the country suffering such attacks.
In 1990, the European Parliament passed a resolution condemning Gladio. The resolution requested full investigations and a total dismantlement of the paramilitary structures involved—neither of which have come to pass. In the middle of what might otherwise have been a more massive media response, headlines were stolen by the US invasion of Kuwait.
Throughout the period of their operation the Gladio cells enjoyed close cooperation from the respective secret services and judiciary. It now being apparent that the Soviet menace was vastly overblown as part of the same “strategy of tensionâ€, the main aim of the terror network operating in Europe was to not only influence public opinion against left-wing sympathies, but to set the stage for further operations in synthetic terror, this time with Islam as the target. As far as Gladio is concerned, the “stay-behind army†motif was basically a cover story, allowing plausible deniability should the network ever be exposed. Which is exactly what happened.
1.4 The Official Scenario
There are minor variants of what might be called the official scenario or story, but we will adhere in this section to the elements held in common to all.
Following the attacks of September 11 2001, various details quickly became available through the media over the next 24 to 48 hours. Alert citizens would have found much to puzzle over in the story as it came together, however. For
example, although it took the FBI several years to track down its last undoubted terrorist — the Unabomber — it took only a few hours to come up with the names of 19 hijackers, all of them alleged to be Muslim fanatics, most of them from Saudi Arabia. The story told of the fanatics seizing control of four aircraft, all but one of the planes being flown into their respective targets. The exception, UAL Flight 93, crashed after “brave passengers†rushed the cockpit to wrest control from the hijackers. The aircraft that crashed near Shanksville, PA, was said to be Flight 93.
|
|
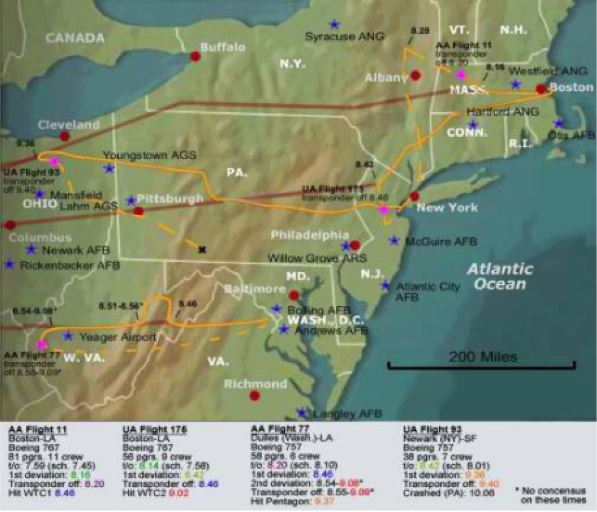
Figure 1: Media map that accompanied the Official Conspiracy Theory |
|
Details of events aboard the respective aircraft came primarily through cellphone (not airfone) calls placed by passengers to persons on the ground, mainly friends and relatives. The alleged content of the calls enabled the White House to fill out
the official story to include Arabs wearing red headbands, brandishing boxcutters, and screaming religious slogans. In view of this claim, alert citizens might have wondered at the leniency of the fanatics in allowing so many passengers to make the calls. The hijackers were apparently unaware that passengers could relay details of their position to the ground, thence to NORAD.
Other, more reliable details came from air traffic control centers that were attempting to track the flights. A colorful map in USA Today showed the routes allegedly taken by the hijackers aboard their respective aircraft. The flights left Boston, Newark and Washington for points on the west coast. (USA Today 2001) Consequently, all four aircraft were flying west when hijacked. Instead of turning for their targets, two of the aircraft continued to fly west, one of them nearly halfway across the continent, before turning back to the east for their Kamikaze missions.
As we shall presently see, the above flight paths are not single, but composite, with different aircraft substituted for the originals at some point in the respective journeys. In particular the flight path of UAL 93 passes very close to Cleveland, where one of the airliners landed under a different name.
The OCT claims that at various points in their respective flights, all four pilots turned off their transponders, apparently under the impression that this would fool the radars at NORAD (which routinely tracks aircraft with no transponders). The apparent incompetence of the hijackers contradicted the White House assessment of a “sophisticated†operation. But such anomalies were sidelined by the drama of the day and its aftermath, leaving a backdrop painted with the sallow faces of 19 dark, unshaven boogeymen.
2. The Evidence Checklist
One may compare the official scenario with Operation Pearl in terms of how well the respective stories account for (or are consistent with) the evidence. We include here several major aspects of the attacks not addressed in any meaningful way by the 9/11 Commission. (NatComm 2004) This also has the useful effect of illustrating just how serious the gaps in the Commission’s coverage really are. (Griffin 2005)
1. The Hijackers: a) not on AA or UA flight manifests
b) unable to fly even light aircraft c) taking westward excursions before turning to targets d) behaving in totally unislamic fashion
2. Air force inaction 3. Transponders turned off 4. Destruction of WTC buildings 1, 2, and 7 5. Absence of significant debris at: a) the Pentagon
b) Shanksville PA 6. Impossibility of high-altitude cellphone calls
It should be mentioned that for each major item in the list above, many minor ones exist, as well. Before continuing, we will explain for the reader unfamiliar with these threads what they mean and how they are supported.
The Hijackers:
a) None of the flight manifests of United and American airlines, as posted on the web in the days and months following the attacks, showed the names of any Arab hijackers, all names appearing to be genuine passengers who expected to arrive at their respective destinations. (CNN 2001) (See also (North 2001)) (In 2007 both airlines published revised lists to which the names of alleged hijackers have been added.)
b) The alleged pilot of AAL 77, Hani Hanjour, tried to rent a light aircraft a few weeks before September 11. The rental manager refused to rent the plane to Hanjour when a cockpit check revealed that Hanjour didn’t seem to know what half the instruments were for. (Goldstein 2001) (Rivero n. d.)
c) The stupidity of the flight paths taken by the respective aircraft before turning for their targets makes the whole idea the subject for satire, as in this little vignette by SPINE researcher Brad Mayeaux, in which Mohammed Atta addresses the other 18 would-be hijackers:
"Ok boys, obviously you’re going to be a little stressed about this mission. So what I’ll say to you is this. Chill. Don’t stress about getting to your targets quickly . . . wait a while before starting the hijack, then if you want to fly away in the opposite direction for a while, feel free. Leave yourself plenty of time to change your mind, after all, suicide and mass-murder is a pretty heavy trip."
d) The alleged ringleader, Mohammed Atta, lived a life that was far from Islamic while in “flight training†in Venice, Florida. He boozed frequently, entertained lap dancers, and lived with a pink-haired floozie named â€Amanda.†(CR 2005), (BFN 2004) This behavior would earn Atta a one-way ticket to hell, according to Islamic belief. And there would be no reprieve arising from either the fatal sin of suicide (forbidding the act at any time for any reason, even in military situations) or the equally fatal sin of harming innocent civilian populations. (Dewdney 2005) It is simply inconceivable and contradictory in every meaningful sense to suppose that an Islamic “fundamentalist†would be unaware of these dictates, let alone failing to observe them to the letter. The sole argument against this position insists that Atta was trying to “blend in.†On the contrary, he stood out and seemed to be making every effort to do so, arguing loudly in a bar about “payments,†(MCMN 2002) glowering at just about everyone he met, and just so that no one would miss the point, leaving a Qur’an on a bar in a Daytona strip club! (CBS 2001)
Air force Inaction:
Many times every year, a commercial or private aircraft strays off course for one reason or another. At such times, when an air traffic controller sees the off-course aircraft, he or she notifies the FAA and NORAD. It rarely takes more than ten minutes for an interceptor to appear off the wing of a straying aircraft. (Anderson 2001) The time-to-intercept has not varied in the hundreds of intercepts made before 9/11 nor in the dozens that have occurred since 9/11. (NYCA 2007) With up to an hour and a half to intercept the off-course aircraft, the inaction by the air force can be called either a stand-down or a de facto stand-down. As it later turns out, Vice President Dick Cheney had, two months before the event, taken on the authority to scramble interceptors in the event of an attack. (Marshall 2006)
This seems the natural place to add the now famous interchange between Cheney and an aide who would periodically enter the Presidential Operations Center as an unidentified aircraft sped toward Washington. Norman Mineta was present and later gave this testimony to the 9/11 Commission (Jones, A 2005)
“During the time that the airplane was coming into the Pentagon, there was a young man who would come in and say to the Vice President…the plane is 50 miles out…the plane is 30 miles out….and when it got down to the plane is 10 miles out, the young man also said to the vice president “do the orders still stand?†And the Vice President turned and whipped his neck around and said ‘Of course the orders still stand, have you heard anything to the contrary?’â€
Transponders Turned Off:
The official scenario provides no good reason for the alleged hijackers to have turned off their transponders. It is well known that NORAD can track any aircraft, whether it has a transponder or not. (Soviet bombers would not have been carrying transponders.) Thus the absence of a transponder signal would offer little protection to would-be hijackers. One could add as a corollary to this observation that none of the four airline pilots involved in 9/11 saw fit to trigger their hijack radio alert, which can be done swiftly, surreptitiously, and without any effect that would be obvious in the cockpit. However, inactive transponders have a definite role to play when it comes to the technique of “radar-swappingâ€. (See below.)
Destruction of WTC buildings 1, 2, and 7:
The official scenario fails completely to explain why the WTC buildings came down. As pointed out in many reliable sources, a jet-fuel (kerosene) fire that last only a few minutes is not, by itself, sufficient to melt or even weaken significantly the structural steel of a modern office tower, especially ones so massively supported as the twin towers were. (Jones, S 2005) (Mitchell 2007)
Absence of Significant Debris:
Neither the Pentagon nor the Shanksville crash sites show the aircraft debris that would normally be expected, either in a building impact or a ground impact. The area immediately adjacent to both sites is a smooth lawn and open field, respectively, both remarkably free of debris. No significant aircraft part can be seen in any of the many FEMA (and other sources) photos taken on the day, the only important exception being a) an engine discovered just outside the Pentagon and b) a piece of skin from the upper fuselage with a portion of the word “American†written on it. Unfortunately, the engine has been identified as a J2D engine, much too small to power a Boeing heavy aircraft and the background color on the aluminum skin is blue, not silver, as it should be for an American Airlines Boeing 757. We construe the latter item as salted, that is, deliberately introduced into the crash scene. (Omholt 2004) (Dewdney & Longspaugh 2004)
Impossibility of HIgh-altitude Cellphone Calls:
It has been proved conclusively by a series of aerial experiments that cellphone calls are impossible to make from high-flying commercial aircraft such as Boeing
757s and 767s. Cellphone networks were designed for terrestrial (surface) communications only. The response profiles have been mapped as a function of altitude, showing connection failures starting at about 2000 feet, then steadily worsening with altitude and culminating in an absolute ceiling for light aircraft at approximately 8000 feet, and an absolute ceiling for light, twin-engine aircraft at about 7000 feet. A large collection of anecdotal evidence indicates an absolute ceiling for larger aircraft, such as the Boeing 757 and 767, at 2000 feet or less. The general rule is this: the heavier the aircraft, the lower its cellphone ceiling. (See the cellphone articles on this site.)
3. The Main Techniques
The following techniques amount to a kind of black-op tool kit for use in a great variety of “terrorist†attacks of the general type of which 9/11 would serve as an example. It will shortly be clear that such techniques would be available only to governments agencies and institutions, primarily intel and security bodies.
3.1. The War-games Cover
Domestic war-games have generally involved scenarios that the nation is under attack by a foreign power. Some aircraft simulate the attackers and some simulate the defenders in the hope that inefficiencies and coverage problems are cleared up before an actual event. To make the simulation realistic, the defenders are not told the plans of the attackers prior to or during the exercise. The response to the simulated attack is carefully scrutinized by military observers hoping to improve air defenses. Such war-games involve not only close cooperation between NORAD and the air force, but with the Federal Aviation Administration (FAA), air traffic control (ATC) centers, and airport authorities. For reasons of air safety, ATC centers must be informed of the anomalies about to appear on their radar screens in order to avoid distracting them from the important job of monitoring and directing the flights of aircraft carrying thousands of human lives.
War games are very expensive to stage and are held only infrequently.
With war games in progress there is an opportunity to create confusion and delayed response times. Early in the morning of 9/11 there were four apparently legitimate flights heading for the west coast and about to experience what would appear to be genuine difficulties. Meanwhile, there were several other non- legitimate (simulated) passenger aircraft clogging the NORAD radars and these
flights were experiencing only simulated hijackings.
During such an exercise normal intercept procedures are set aside and the automatic response — that would have guaranteed the appearance of a fighter aircraft off the wing of each hijacked airliner within 10 minutes or less of notification — was thwarted, in effect. (Had fighters actually been sent up in timely fashion, their pilots would have seen some strange sights — presently to be described.)
To use such war-games for cover in an operation like 9/11, the real perpetrators would arrange that one set of aircraft simulate hijacked planes being flown into prominent national buildings, while the other set of aircraft try to defend against such a terrorist attack. Because it involves the airspace over which it has jurisdiction, the FAA is informed of the exercise, as well as air traffic managers who are informed of the exercise for the reasons outlined above.
The command post for the war games was the NEADS Center, operating out of a hanger on an abandoned airfield in New York State. Apparently, all calls from ATC personnel were routed to the NEADS Center, instead of the usual FAA/NORAD chain of command. Although NEADS was under the direct control of NORAD, it may have had a free hand, so to speak, for the war games ongoing that day. NEADS did not have either the resources or information to mount an effective fighter defense, being solely concerned with progress of the war games and following that script. Much of the confusion and inaction was the natural result of relocating the North American Air Defence Command to the NEADS Center on that fateful day. The outcome was entirely predictable and, therefore, subject to control.
At least nine and possibly up to 20 major overlapping war game exercises had been scheduled for September 11, 2001. Here are nine of their names:
Amalgam Virgo Amalgam Warrior Apollo Guardian Crown Vigilance Global Guardian
Northern Guardian Northern Vigilance Vigilant Guardian Vigilant Warrior
One attack scenario, Amalgam Virgo, involved aircraft being hijacked by terrorists and flown into public buildings. On the morning in question, ATC knowledge of the games was reflected in conversations between ATC personnel and military liaison officers such as the following call placed at 8:37 am to the Northeast Air Defense Sector (NEADS):
Boston Center: “Hi. Boston Center T. M. U. We have a problem here. We have a hijacked aircraft headed towards New York and we need you guys to — we need someone to scramble some F-16s or something up there, Help us out.â€
Military (Tech. Sarg, Jeremy Powell at NEADS) : “Is this real-world or exercise?â€
Boston Center: “No, this is not an exercise, not a test.â€
In this particular case it is evident that ATC knew about the exercises and would be able to distinguish a war-games hijacking from one apparently being executed on one of the airliners in their control sector. Fighters were never scrambled for the flight in question (AAL 11), the excuse being that interceptor aircraft were already deployed elsewhere in the war game exercises. (This was not really true, there being fighters still available at Langley and Otis air bases.)
The war games scenario also opens nearly limitless possibilities for getting administrative and technical personnel at airports to do things they ordinarily wouldn’t do. For example, one can arrange for takeoffs and landings of aircraft that are part of the exercises. Under the veil of secrecy that necessarily attends some of the exercises, only the upper level airport management would need to know that a particular aircraft — that might otherwise raise concerns on the part of control personnel — was part of the exercise and could be cleared for landings or takeoffs with a word from the management person in question. It should be stressed here that such cooperation by an airport manager would in no way make him or her either complicit in the overall operation nor necessarily suspicious of its true nature, even in the wake of 9/11.
Thus an airliner that might or might not be empty of passengers could be playing the role of an aircraft that would be “hijacked†as part of the war games. It could land or take off from virtually any airport selected by the planners of Operation Pearl. Indeed, the distinction between the two types of hijacking could be blurred in that a single aircraft could be playing both roles simultaneously.
Here is a “cleaned†transcript of the NEADS tape (Monty 2011) Note the
unprofessional and almost irresponsible behavior of the NEADS personnel as they come to grips with an event that they may well think is just another staged war exercise. (Bronner 2006)
08:37:52 BOSTON CENTER: Hi. Boston Center T.M.U. [Traffic Management Unit], we have a problem here. We have a hijacked aircraft headed towards New York, and we need you guys to, we need someone to scramble some F-16s or something up there, help us out.
POWELL: Is this real-world or exercise?
BOSTON CENTER: No, this is not an exercise, not a test.
8:37:56 WATSON: What?
DOOLEY: Whoa!
WATSON: What was that?
ROUNTREE: Is that real-world?
DOOLEY: Real-world hijack.
WATSON: Cool!
[advance tape]
08:37:58 P.A.: Major Nasypany, you’re needed in ops pronto. Major Nasypany, you’re needed in ops pronto.
[Recorded phone line:]
SERGEANT MCCAIN: Northeast Air Defense Sector, Sergeant McCain, can I help you?
SERGEANT KELLY: Yeah, Sergeant Kelly from Otis, how you doing today? SERGEANT MCCAIN: Yeah, go ahead.
SERGEANT KELLY: The – I’m gettin’ reports from my TRACON [local civilian air traffic] that there might be a possible hijacking.
SERGEANT MCCAIN: I was just hearing the same thing. We’re workin’ it right now.
SERGEANT KELLY: O.K., thanks.
The whole transcript gives the impression of a folksy, down-home air defence operation, with personnel displaying an attitude of casual unconcern. It could not contrast more sharply with the sophisticated, rapid, and protocol-laden procedure normally followed by NORAD and the FAA.
3.2 Radar Swaps
Air Traffic Control (TRACON) operators see all aircraft flying in their sector on a computer screen on which is displayed geographical information (boundaries, coastlines, etc) as well as all aircraft flying within that airspace. The map below displays all the control sectors in the continental US.
|
|

Figure 2: “Area Control Center†Source: Wikipedia |
|
For example, the control sector labeled ZDC includes Virginia down to North Carolina and west to West Virginia. Washington DC is marked in red. This sector has dimensions of approximately 450 mi (N/S) by 300 mi (E/W). If one divides the N/S dimension by the number of lines on a standard computer display screen (1024), a distance of 0.43 miles or about 2200 feet.
Two aircraft having this separation will appear as two blips on the screen, but aircraft closer together than this will appear as one. Radar operators (i.e., air traffic controllers) are the only people who are aware of what aircraft are presently in the sky and where they are going. The vast majority of people are completely unaware of such details and, when an aircraft passes overhead, can usually not tell one type from another, let alone what airline or aviation company may own it. This observation, while something of a commonplace, has important implications. If an organization wishes to substitute one aircraft for another without anyone knowing it, the only people it has to deceive are the air traffic controllers.
In other words, as soon as two aircraft get within 2000 feet of one another, there would be a tendency for their respective blips to merge. With a smaller separation, the two aircraft could easily appear as one.
Of course, two aircraft that are that close together run a certain risk of collision – unless they are at different altitudes. Radar screens are two-dimensional in that they represent airspace in the same way as a map does, with the vertical dimension of altitude suppressed.
Every commercial passenger jet carries a transponder, a device that emits a special radio message whenever it senses an incoming radar wave. The signal carries the transponder code that appears on ATC screens as a “data tag,†a small four-line block of text that appears on the controller’s screen, as in the following example:
UAL 93 375 309 NWA LAX 884 FE 3
flight identifier altitude (100s of feet) & airspeed (knots) origin and destination airports other data
The purpose of the code is to make it clear to ATC operators which plane is which. Other information sent by the transponder includes the altitude at which the aircraft is flying. Transponders were implemented many years ago precisely
for the reason that radar blips are otherwise easily confused. Transponders make the controller’s job much easier. (WIKI 2008)
The pilot of an airliner can turn the transponder on or off in the cockpit. He or she can also change the code by keying in new numbers. It takes a pilot less than a minute to key in a new code — or less than a second to turn the unit off. Without a displayed altitude number, it is impossible for a radar operator to tell whether two merged blips represent a potential collision or not. The data tag is displayed if an aircraft’s transponder is turned on, otherwise, the radar operator has no idea of the altitude at which an aircraft happens to be flying.
If one aircraft happens to be within half a kilometer of another, above it, below it, or even slightly behind or ahead of it, the radar operator will see only one aircraft, as long as the two maintain a horizontal (plan view) separation that is no greater than 2000 feet.
Imagine now two aircraft, both headed for the same approximate point on the radar screen, both with their transponders turned off. One is well above the other but, as the blips merge, both planes swerve, each taking the other’s former direction. The operator would simply see the aircraft cross and would have no way of realizing that a swap had taken place. This could be called an “X-swap,†since the maneuver is intended to make a radar operator think that the two flight paths had actually crossed each other.
There are many other swapping patterns available. For example, one plane could apparently catch up and “pass†another when, in fact, it slowed after the blips merged, even as the other speeded up. Such a swap could be called an “I-swap,†since all the action takes place along a straight line.
Another method involves the replacement aircraft climbing out of a valley where it would be invisible to distant radars, even as the other aircraft descended into the valley. Again, a radar operator would see a more or less seamless flight without realizing that he or she had been momentarily seeing not one, but two aircraft on the radar screen.
Of course, if the transponders are turned on, as explained in the next section, such confusion is unlikely to occur. Even in this case, however, the deception can be complete if the aircraft switch transponder codes.
19
Finally, in a few parts of the United States there are areas termed radar “blind spots†because, owing to topography, radar coverage is poor to nonexistent. In such areas swaps may be made far more easily. One such area exists in southwestern New York state.
3.3 Remote Control
An onboard remote control system of the type used in this scenario employs a signal interface that does two things: It reads signals from a ground station and sends signals back to it. Both sets of signals must pass through the aircraft’s antenna system. In the Boeing 757 and 767 the antenna system is located in the forward belly of the aircraft.
The outgoing signal from the aircraft would include a video feed from a camera located in the nose or other forward portion of the aircraft. Flight data such as control positions, airspeed and other instrument readings are also included in the outgoing signal. The incoming signal from the ground station would include the position of a virtual control yoke (governing direction of aircraft), thrust, trim, and other essential flight parameters).
The virtual pilot sits in front of a reduced instrument panel and a video monitor. A simplified control yoke or “joystick†control is also part of the operator’s equipment. The remote pilot would watch the instruments, as well as the video image, making continuing adjustments in the aircraft’s flight path, just as if he or she sat in the cockpit of the actual aircraft.
An aircraft with such a remote guidance system (SPC 2000) can be made to behave like a piloted airliner in every particular. This includes engine start, pullback, taxiing, awaiting instructions with engines running, turning onto a main runway, pausing, then proceeding into a normal takeoff pattern of behavior. Radio traffic can be conducted from a nearby operation and not necessarily from the aircraft since (in the absence of radio direction finding equipment) nobody would have any idea that a radio signal is not actually coming from an aircraft.
Many claims of the attacking aircraft being under “remote control†have appeared on the web since 9/11, but typically with little or no supporting documentation. The claim of a pre-installed anti-hijacking system has proved impossible to verify.
Remote control systems fall into two types: aircraft-specfic systems such as the Global Hawk technology (USAF 98) and general control systems that can be fitted to a variety of aircraft. As it happens, Global Hawk does not have a remote human operator; instead, onboard navigation electronics guide the vehicle to its target.
One should include in this list of possibilities the Predator unmanned surveillance vehicle (USAF 2003), a modularized aircraft that can be broken into components for ease of shipping and rapid deployment. One of the components includes a remote guidance module which might be refitted to another aircraft with appropriate modifications. The Predator operates under remote human guidance from a ground station that, once deployed, would require as few as two human operators during a “secure†operation. These are presumably the aircraft described as “drones†in Middle Eastern theaters of operation.
A more realistic possibility involves an item of complicated hardware and electronics known as a “flight termination system,†manufactured by the System Planning Corporation. (SPC 2000) (See Note 3.) This system permits remote, “hands-on†control of a nearly endless variety of aircraft, the control interface being to a large degree customizable.
Without question the basic technology for the remote guidance of aircraft has been on hand for many years, apparently dating back to Operation Northwoods days. It would be a straightforward technical operation to install a remote control system in virtually any type of aircraft, whether a large commercial airliner or anything smaller. The aircraft carrying the installation would be available and prepared in advance, then substituted by a radar swap for the passenger aircraft it was meant to replace.
3.4 Disposal of Bodies and Aircraft
This final, grisly component of the day’s operation to consider is the “disposal†of passengers from the four flights in question. In this area of the inquiry, we must consider two possibilities. Although a majority of the 258 passengers and crew members involved in the flights would be real, some of them may have been fake. In other words, some of the passengers may have been traveling under false names as chaperones to subdue other passengers who became unruly or suspicious during the disposal operation.
A planeload of passengers that landed at a specified airport would be deplaned in a secure area (remember the war games) and transferred either to buses or to a plane
on the promise of a continuation of their flight. Of course, fake passengers would rejoin their operating unit at this point.
Once passengers have boarded the buses or plane, colorless, odorless sarin gas could be injected into the ventilation system and within five minutes everyone would be dead. In the case of bus transportation, the bodies would be transferred to a closed transport trailer and trucked to a crematorium to be reduced to ash, which is much easier to dispose of than flesh. In fact, the safest disposal site for the ashes would be to add them to the debris from the World Trade Center buildings, either on site or at the Staten Island Landfill site. There, officers assigned to the duty of finding human remains would not be surprised to run into occasional patches of human ash.
In the case of airplane disposal, there are two possibilities: the airliner could be flown out over the Atlantic beyond the continental shelf, splashed down on the ocean surface gently enough to avoid tearing the aircraft apart, then sunk as holing charges were detonated, allowed every part of the plane to fill with water and sink to a depth of approximately 2000 meters, well beyond the operational range of conventional or nuclear submarines. Such an aircraft would, of course, be operated remotely. Aircraft themselves (with or without passengers) could be flown to the “scrap yard†at Davis-Monthan airbase where they would be stripped, recycled in part, the rest sold for scrap. (GS 2005)
It should be added that before any bodies were gone forever, workers would be careful to remove tissue samples of one kind or another. In some or all cases, these remains would then be subsampled to provide corroborating matches when necessary. (See section 5.)
(The author apologizes to families of 9/11 passengers for including such details, but revealing the true nature of Operation Pearl, as a matter of (genuine) national security, must have priority over private griefs and the pain of personal loss.)
4. The Operation
The actual operation, as outlined here, is divided into three main phases: preparation, execution, and follow-up. The descriptions appearing here are necessarily partial since we are obviously not privy to many of the actual details. However, much of what follows is guided by a combination of technical feasibility and reported anomalies that, in some cases, provide clues about part of the operation.
4.1 Preparation
The preparation phase of Operation Pearl is further subdivided into four subsections that focus on the Hijackers, the World Trade Center, the drone aircraft, and making special arrangements to facilitate the attacks.
4.1.1 The Hijackers
According to official sources (FBI 2001), the 19 alleged hijackers were:
American Airlines #77
American Airlines #11
United Airlines #175
United Airlines #93
Khalid Al-Midhar Majed Moqed
Nawaq Alhamzi Salem Alhamzi* Hani Hanjour (pilot)
Satam Al Suqami Waleed M. Alshehri* (pilot) Wail Alshehri* Mohamed Atta (pilot) Abdulaziz Alomari* (pilot)
Marwan Al-Shehhi (pilot) Fayez Ahmed
Ahmed Alghamdi Hamza Alghamdi Mohand Alshehri*
Saeed Alghamdi* Ahmed Alhaznawi Ahmed Alnami* Ziad Jarrah (pilot)
Of these 19 â€hijackers,†some seven (marked with an asterisk above) appeared to not only have survived their respective crashes, but in at least one case strongly objected to being on the official list in the first place. (WRH 2007) This would leave the hijacking operation seriously undermanned. However, given that no hijackers were actually aboard the airliners in question, it would seem obvious that authorities would need a list for public release in short order. Some of the would- be hijackers were undoubtedly trained for the job — at least to the extent of registering for flight school in Florida — but names would be needed to flesh out the list. The operation of adding names was sloppily executed and the perpetrators seem to have depended on the mainstream media not to make an issue of it.
As for the “genuine†hijackers, some four are known to have taken flight training at a flight school in Venice Florida and elsewhere. According to the owner of one of these schools the Arabs training at his school were simply unfit to fly large passenger aircraft of the types used in the attacks of 9/11. (Monaghan 2007) When Hani Hanjour, alleged pilot of Flight 77, tried to rent a Cessna less than a month before the attack, the flight instructor refused the rental when an instrument check revealed that Hanjour did not seem to know what any of the instruments were for. (Gaffney 2009) (Muga 2010)
4.1.2 The World Trade Center
The World Trade Center complex of buildings was the brainchild of brothers David and Nelson Rockefeller who suggested the project to the Port Authority of New York in the 1950s Their suggestion was adopted and in the 1960s the architect Minoru Yamasaki was engaged to design the twin towers. Construction of the World Trade Center towers began in 1966, with Building 1 (the north tower) coming to completion in 1970. Building 2 (the south tower) was ready for tenants by 1972. The total cost of the project to the sponsoring New York Port Authority was $900 million. (WK-WTC 2008)
There are two differing claims about the nature of the “core†of the building, a massively built structure that took the main bearing weight of the building, assisted by a perimeter of lighter steel box columns. The majority opinion, as specified by the National Institute of Standards in Technology (NIST) and used by a majority of 9/11 research groups, maintains that the core consisted of a rectangular configuration of massive box-columns. In such a scheme, the box columns might be filled with concrete, but concrete was otherwise used mainly for the construction of elevator shafts, poured floors and other structural features not involved in load-bearing.
Another claim (Brown 2008) describes a rather different structure in which the cores were essentially concrete structures, a set of four adjacent rectangular tubes
configured as one large rectangle, with the box columns adjacent to and reinforcing the concrete walls. In cross-section, this version of the core had four inner walls in the shape of a + sign, with the walls meeting in the middle. This alternate core design would involve far more concrete than the official one, several orders of magnitude more. Either way, the core took almost the entire load of the building, a perimeter of lighter box columns bearing the outer wall load and providing additional stability to the building.
An essentially concrete core would also have to be kept secret, should the need ever arise to explain the collapse of the buildings as due to fire effects. Concrete would be impervious to fire. As it happens, even during construction of the towers, plans were checked out for the week then locked up for the weekend following each week’s construction work.
In covering all the possibilities for the destruction of the towers by explosives, there are essentially two windows of opportunity for planting explosives. The first possibility involves planting the explosives during construction. The second possibility allows for a clandestine operation conducted over a year or two prior to 9/11, the planting of high explosives on every other floor of each building.
This scenario does not need to commit to either time period, there being no obvious reason to choose one over the other. It is interesting to note, however, that during cement-pouring operations in the 1960s, there is an unverified claim that videographers documenting the construction were not allowed to film a certain phase of the operation in which “government crews†took over from regular construction workers. Their alleged role was to apply a special “vibration- resistant coating†to the three-inch rebar rods reinforcing the concrete core structure. The coating was claimed to be flammable. Armed guards prevented anyone but the government crew from having access to the rebar — which was kept under lock and key. The government insisted that only a special crew could handle the coating, owing to its flammable nature. Not only was such an operation unprecedented in steel tower construction, it is difficult to understand why secrecy would in any way be essential to it.
Under this portion of the overall scenario, it remains an open question whether the “coating†involved was actually a high-yield plastic explosive like C4, as claimed by Brown, or nanothermite. We lean toward the latter possibility since the finding of nanothermite in dust from the World Trade Center explosions appears to be quite solid. (Jones 2009) (Harrit 2010). Thermite packs would also have to be installed near the bases of the main support columns to ensure a clean collapse. Evidence of such an operation can be seen in the following image, taken during the cleanup phase.
|
|

Figure 3: angular cut to heavy box-column |
|
In any case, if the building were ever to be brought down in the future, it would only be necessary to install detonators, one or two per installed strip, at any later time within the “shelf life†of the explosive. Each explosive element in the overall rigging plan would end at a point that would later be accessible through a special port in the concrete. A later wiring operation would require far less time than rigging-plus-wiring.
The second possibility would involve crews working primarily during evening and night hours to plant explosives close to the core columns, either on each floor or every other floor. Large, unrented office suites were common throughout either building and any could be the base of operations for certain phases of the rigging operation.
Like any well-executed controlled demolition (even with the addition of exotic incendiaries) this one had a timing circuit, most likely involving only a computer and a radio transmitter. Each detonator could be triggered by an electronic code specific to that device. Alternatively, a single pulse might initiate timers to begin a countdown so that explosions would occur in a downward sequence at nearly free fall speeds.
4.1.3 The Drone and Decoy Aircraft
This section covers not only the “drone†aircraft, those under remote control, but piloted aircraft taking part in radar swaps, as outlined earlier. In the first category are the aircraft involved in the four crashes. Without committing to any of the following possibilities, one may nevertheless list them as follows:
WTC 1 WTC 2 Pentagon Shanksville
smaller aircraft of unknown type Boeing 737 Global Hawk or Skywarrior cruise missile
The only imagery available for the crash at WTC 1 (north tower) is the “Fireman’s Video†shot by the Naudet Brothers, a French film crew making a documentary about the NYFD on the morning of September 11 2001. The video is very much out of focus and shows a vague, whitish/grey aircraft shape impacting the north tower. Early reports of a “commuter plane†(Salvador 2002) being involved in the collision widen the possibilities from an aircraft of this size up to and including a full-size passenger jet or military aircraft. The Naudet video would include this possibility, thanks to the lack of focus.
Based on the description by Mark Burnback, a reporter for WCBS/Fox News who stood on the “wrong†side of WTC2, the side from which the windows of the banking aircraft would be visible, said the aircraft had no windows at all, was painted in military gray livery and had a blue logo on the nose. (Fox 2001) Other eyewitnesses close to the scene conform the military gray and complete absence of commercial livery. Some surmise that it was a Boeing 737. It had unusual “pods†on the lower fuselage. The engine found on the street later apparently belonged to a Boeing 737. (Carlson 2005) Since there were KC-737 tankers in operation at the time, it seems safe to propose a 737 as a strong possibility for the incoming aircraft.
According to credible eyewitness testimony, the Pentagon attack aircraft appears to be an Global Hawk (USAF 1998) (Bollyn 2006), although we keep open the possibility of an A3 Skywarrior (Schwarz 2005). The profile of the tail that appears in the Pentagon parking lot security video is too small to be that of a 757, but about the right size for a either a Global Hawk or a Skywarrior.
The crater near Shanksville PA is consistent with the impact of a large missile in a shallow dive, leaving a long gouge that was later excavated and widenerd. Since no major aircraft components such as engine, wings, tail, passenger eats, etc were found anywhere near the crash site, we will take our clue from a Vietnam veteran who lived in the area and said he heard an incoming missile just before the crash. Additionally, the “white mystery plane†that overflew the Shanksville crash site just before the impact (McElwain 2001) was also involved in the operation. In this scenario, as mentioned earlier, we take the white aircraft as an A-10 Thunderbolt, based on the description of resident eyewitness Susan McIlwain. This scenario uses the A-10 as the decoy plane posing as Flight UAL 93 to fool ATC personnel and also to carry the flight data recorder that would later be alleged to come from UAL 93. As in the Pentagon FDR reconstruction, this FDR record stops short of the crash, rather than at the point of the crash.
It follows that at least four alternate aircraft were involved in Operation Pearl, three of which would have been fitted with remote control, for example a Flight Termination System (see earlier) well before the morning of 9/11. The aircraft would have been so prepared under the guise of another operation (presumably military) at one or more military bases. The WTC 1 drone, as described earlier, could have taken off from Boston Logan airport in lieu of Flight AAL 11. It was taxied to the gate by a live pilot who activated and tested the control system, locked everything down, then deplaned prior to boarding, which suddenly switched to another gate. The WTC 2 drone flew directly from a military or other base toward its rendezvous point with Flight UAL 175 somewhere east of Cleveland.
4.2 Execution
The following basic timeline lists the flights, numbers of passengers/crew, departure times, all Eastern Daylight time. The “grounding order†mentioned below refers to a general FAA direction that all commercial flights still in the air at the time stated fly to the nearest airport to land. The acronyms UAL and AAL refer to United and American Airlines, respectively.
Flight
AAL 11 UAL 175 AAL 77 FA
UAL 93
pass/crew Departure Deviation Transponder
Hit
8:46 am* 9:02 am 9:37 am 9:45 am
81/11 7:59 am 56/9 8:14 am 58/6 8:20 am Grounding Order 30/7 8:42 am
8:16 am 8:42 am 8:46 am
9:36 am
8:20 am 8:40 am 8:55 am
9:40 am with AAl 11 and working
Each flight is dealt with separately below, starting through the timeline just given.
4.2.1 Flight AAL 11
Flight AAL 11 is alleged to have flown from Boston’s Logan Airport. Just minutes before boarding, the 81 passengers in the departure lounge for AA Flight 11 were informed that there had been a change of departure from Gate 32 to Gate 26. The aircraft waiting at Gate 32 was never boarded, but departed on schedule at 7:45 and took off at 7:59 am. [WB 2004] This could easily have been the drone aircraft that struck the WTC north tower. As pointed out in Section 3.3, some remote control systems allow a complete range of aircraft operation, including pullback, taxiing out to a designated runway, and then taking off, with all radio communication handled from another location.
begin boarding end boarding sched dep. actual dep. takeoff
Gate 32 7:15 7:30 7:45 7:45 7:50
Gate 26 7:35 7:55 8:10
? ?
Meanwhile, passengers were not permitted to board the aircraft at (the new) Gate 26 until 7:35. The departure time of this aircraft is not known, since the aircraft that departed from Gate 32 (Flight 11) is the only one for which a public record exists. Indeed, it is not even known if the passengers boarded a plane at all. For example they could have boarded some form of ground transportation under the impression that it would take them to another aircraft. The official story neglects to mention the change of gate and appears to be incorrect in this particular.
29
10:06 am
Flight AAL 11 was a Boeing 767. Scheduled as a nonstop flight from Boston to Los Angeles and piloted by captain John Ogonowski and first officer Thomas McGuinness, the aircraft had a crew of nine flight attendants. The plane that departed from Gate 32 was assumed by air traffic controllers to be the aforesaid aircraft. After responding to the ATC instruction “20 right AAL11†(a turn to the right of 20 degrees), the pilot was told to climb to 35,000 feet, but made no reply.
As shown in the map on Page 8, Flight 11 followed the intended route until 8:16 am, when it turned to the northwest. A faked cellphone call, allegedly from flight attendant Mary Sweeney at 8:19 am, informed American Airlines that a hijacking was in progress and about a minute later, the transponder on Flight AAL 11 was switched off. If the call was indeed received at 8:19 am (regardless of the origin), American Airlines would immediately have informed both the FAA and NORAD about the hijacking as a matter of standard procedure. The standard intercept time for a scrambled interceptor would be no more than 15 minutes following the notification. Thus, by no later than 8:34, a fighter should have had Flight 11 in view. However, no interceptor even took off until 8:53 am, some seven minutes after an aircraft struck the WTC north tower.
The exact aircraft type that struck the north tower of the WTC complex is unknown. The only evidence of the collision is contained in the famous Naudet Brothers “firemen video.†This was part of a documentary being prepared by a French Film crew on the New York Fire Department. The videographers were filming a fire crew investigating a gas leak a few blocks north of the north tower, when the sound of screaming engines overhead caused the videographer to divert the camera upward to capture a maddeningly out-of-focus view of the impact. (Spencer 2005)
The aircraft thus portrayed, while no larger than a Boeing 767, may have been smaller. Early reports of the strike described a “commuter aircraft,†indicating a somewhat smaller plane. (Noble 2001) (Salvador 2002) The rumor apparently emanated from Fox News (Jones 2001). In this scenario, the plane that struck the north tower was the one that departed from Gate 32 at Boston’s Logan airport, this being the simplest form the operation could take. As mentioned earlier (See section 3.3), a remotely controlled aircraft can imitate a regular commercial flight in all aspects. Presumably this aircraft also produced a fireball like the well- documented south tower strike. In either case, it is not known if this was jet fuel (kerosene) from the aircraft’s fuel tanks or an on-board charge of napalm or the dramatic fuel-air explosive used in Hollywood movies.
30
4.2.2 Flight AAL 77
American Airlines Flight 77 departed from Washington’s Dulles airport at 8:20 am for Los Angeles. The Boeing 757 carried 58 passengers that morning and six crew members. It flew due west over northern Virginia and the state of West Virginia, getting as far as Kentucky when, at approximately 8:55 am, it began a slow southward turn and its transponder was turned off. The pilot did not use the hijacking alert system (which involves entering the code number 7500 in the transponder). The plane continued its gradual left turn until it was heading east, back toward Washington, entering West Virginia by 9:10 am.
Map of Washington Area
At 9:25 am the FAA notified NORAD that Flight 77 was headed toward Washington. Two F-16 fighters were immediately scrambled from Langley Air
31
Force Base in Virginia at 9:35 am. Langley is 150 miles from the Pentagon, Andrews Air base being only 13 miles away.
Two minutes later, at 9:37 am and well before the Langley interceptors could arrive, an aircraft struck the Pentagon. Although the approximate flight path of Flight AAL77 was known from sporadic radar contacts with the airplane, more detailed and precise information was found in the aircraft’s own flight data recorder (FDR), one of only two “black boxes†that were ever found from the four flights. According to the FDR, the aircraft made a wide turn to the right as it approached Washington DC. The turn, combined with a gradual rate of descent, formed a loop, crossing under its previous flight path and coming into line for what would appear to be a run at the Pentagon. But the FDR record ends a full second before impact, the recorded altitude at this point being equivalent to 475 feet above sea level. Since the Pentagon is 125 feet high and 43 feet above sea level, the aircraft would clear the top of the building by 315 feet, flying straight and level. The aircraft, however, was in a dive of nearly 5 degrees and flying at 463 knots (533 mph) at the point of record termination, placing it at approximately 700 to 800 feet (horizontally) from the impact point.
At the given rate of descent, it would be no less than 245 feet above the Pentagon roof by the time the nose of the aircraft would otherwise be penetrating the Pentagon wall. If the plane began to level off at the FDR tape termination point, it’s actual distance above the Pentagon roof would obviously be somewhat above either figure. (Pilots 2007)
The well-known “parking lot video†taken by one of the Pentagon security cameras shows an aircraft much smaller than a Boeing 757 almost skimming the lawn as it sped toward the Pentagon. The track of the object merged with that of the 757, constituting an I-swap. (See Section 3.2) There are two possibilities for this fast-moving aircraft, either an A-3 Skywarrior under remote control or a Global Hawk, the J2D engine found at the Pentagon being far too small to be the power plant for a Boeing 757. (Schwarz 2005) (Bollyn 2009) Given the altitude, attitude and heading of the 757 at the record termination point, there is no possibility of confusion between the 757 and the smaller aircraft in terms of their relative positions. The smaller aircraft came in well to the right of Flight AAL 77 and well below it, far enough away to be visually distinct, albeit close enough to fool radar operators.
In short, controllers thought that the overflight of AAL 77 was merely the smaller plane passing over the Pentagon. In reality, it was Flight AAL 77 that flew over
32
the Pentagon and the smaller plane that crashed into it.
This leaves the question of whether pilot Charles Burlingame was still at the controls when Flight AAL77 passed over the Pentagon. In this scenario, Flight AAL 77 was “hijacked around 9:00 am, when its transponder was turned off. In this case the hijacking would not be carried out by Hanjour & Co., but by an agent or agents traveling as passengers. There was little danger that the hijacker would die when the plane struck the Pentagon, since that was not the plan in any case. Whether the hijacking involved firearms or not matters little, since anyone claiming to represent a major Agency could presumably talk his way into the cockpit.
As Flight AAL 77 approached and passed over the Pentagon, a C 130 military cargo plane was carrying out strange, acrobatic maneuvers in the skies over Washington DC. Many people in the general area of the Pentagon were watching the C-130 as the 757 approached its “target.†Witnesses closest to the crash site in the C-ring of the Pentagon were almost all in cars traveling the beltway that passes along the south side of the Pentagon. At about the time that Flight AAL 77 was obscured by car roofs, the low-flying Skywarrior (or Global Hawk) crossed right over traffic on the Beltway and struck the Pentagon, creating a tremendous explosion. What witnesses will later claim to see will depend on which of these aircraft caught their attention just prior to the explosion. And like all good witnesses, they will “remember†best those details that match the official story.
In the Operation Pearl scenario, Flight 77 cleared the Pentagon building, flying through the rising smoke of the initial fireball and continued on the Reagan International airport, landing without further incident, and then taxiing over to a restricted area. We do not know what happened to the passengers.
4.2.3 Flight UAL 93
United Airlines Flight 93 was a Boeing 757 carrying 30 passengers and 7 crew members from Newark International airport to San Francisco. The most lightly loaded of the four aircraft selected for Operation Pearl, it departed Newark at 8:42 am, climbed out and headed west toward San Francisco. At 9:36 am, nearly an hour into the flight, ATC operators noticed a deviation in the airliner‘s flight path. Attempts to contact the aircraft failed and a few minutes later the plane’s transponder was turned off. At 10:06, according to the official story, the flight crashed near Shanksville, a small rural community in southeastern Pennsylvania in
33
the middle of a hilly, heavily wooded area.
The aircraft’s flight path, according to the official story, took it west as far as Cleveland. There, it appeared to veer sharply to the south, flying more or less directly toward Washington, DC. (Pilots 2007)
In Shanksville, the crater made by the incoming aircraft was completely inconsistent with the crash of a large passenger liner (Killtown 2006), with no significant debris of any kind, only a few metal fragments that would be more consistent with a cruise missile impacting the ground at a shallow angle, leaving a long, shallow gouge in the earth. In fact, an aerial view of the crater shows a vee- shaped gouge, the sharp end being the point of entry for the missile, as shown here.
Alleged crash site of UAL 93 shows uncharacteristic gouge
One aircraft engine was located in the woods a half mile away. There is no report of a second engine ever being found in the area. Combing the general area for
34
miles, residents of surrounding Somerset County discovered a few human remains, some items of clothing, as well as several copies of United Airline’s in- flight magazine recovered near New Baltimore, eight miles downwind from the crash scene. No luggage, seats or whole bodies were ever reported found. No traces of jet fuel were detected by the EPA in a later investigation of the crash site. (Pilots 2007)
Although some researchers explain the debris field by hypothesizing that Flight 93 was shot down or experienced a crisis that caused it to break up in midair, the pattern and amount of debris is more consistent with a high-altitude salting operation in which a cargo aircraft, such as an old C-119 Flying Boxcar (with rear offloading bay), would have carried a selection of debris (including body parts– see Section 5). The ejection of debris would have to take place within as short a time as possible, in order to keep the pattern tight on the ground.
Finally, several Shanksville residents saw a mysterious white plane pass overhead at a very low altitude just prior to the explosion, close enough for details of its size and configuration to be clearly visible to residents, two of which lived near the crash site and claimed to have heard a sound like an incoming missile. (One of these was a Vietnam veteran.)
Shanksville resident Susan McElwain watched the white aircraft pass directly over her mini van: “It came right over me, I reckon just 40 or 50 feet above my van,†she recalled. “It was so low I ducked instinctively. It was traveling real fast, but hardly made any sound. Then it disappeared behind some trees. A few seconds later I heard this great explosion and saw this fireball rise up over the trees, so I figured the jet had crashed. The ground really shook. So I dialed 911 and told them what happened . .
“There’s no way I imagined this plane – it was so low it was virtually on top of me. It was white with no markings but it was definitely military, it just had that look. It had two rear engines, a big fin on the back like a spoiler on the back of a car and with two upright fins at the side. I haven’t found one like it on the internet. It definitely wasn’t one of those executive jets. The FBI came and talked to me and said there was no plane around.†[McElwain 2001]
There is only one aircraft in the world that matches the description given by McElwain. The A10 Thunderbolt has two rear engines and twin outboard stabilizers on the tailplane. (McChord, 2003) This scenario uses the A-10 as the
35
decoy aircraft, following a radar swap south of Cleveland. Flying without a transponder, this aircraft would result in a blip on ATC radar screens that was indistinguishable from that of a heavier aircraft like the Boeing 757. The possibility emerges that the shadow aircraft would replace UAL 93 in more than one way; it would not only follow the alleged flight path of UAL 93, it would perform all the maneuvers associated with the on-board struggle that forms such an important part of the official story. It’s own flight data recorder (FDR) could later be added to the crash site or “found†there. As it is, the National Transportation Safety Board made an animation video of a plane behaving exactly in accordance with the information on the FDR tape. As in the Pentagon case, the plane is too high at the time of the crash to be involved in the crash. (Pilots 2007)
The following scenario for Flight UAL 93 is based on some strange goings-on at Cleveland’s Hopkins International airport. We do not claim that our interpretation of these events is in any way definitive, only that the “emergency landings†at Cleveland are precisely what we would expect for any of the four flights following a radar swap, especially in the context of ongoing military exercises. The following summary is based on research by the investigative Group called Team 8. (WB 2004)
Around 10 am, tower personnel at Hopkins airport received word that Delta Airlines Flight 1989 was coming in for an emergency landing with a possible bomb on board. The airport terminal building, as well as the FAA building and a large NASA facility were all evacuated. DAL 1989 landed at 10:10, taxied to a remote area near the FAA building (beside the I-X Center) and sat there until 12:30, when an “evacuation†of the 69 passengers began.
If Flight UAL 175 had proceeded directly from Boston to Cleveland, instead of turning south, as the official story alleges, it would be landing at this very time in Cleveland, having traveled at an average speed of 310 mph (takeoff & landing allowance included).
Strangely enough, a second Flight, thought to be DAL 89, came in for a landing at 10:45 am with little excitement. It proceeded to another remote area of the airport, beside the NASA Glenn Research Center. At 11:15 about “200 passengers†were evacuated into the Center.
If Flight DAL 89 was one of the aircraft being used in the ongoing war-games exercises, this would explain the confusion that surrounds its real identity. Thus
36
anyone remaining in the (partially) evacuated tower would at least see a Delta airliner land on the main runway. When DAL 89 was first cleared to land, it was apparently not in the correct position to land easily and found it necessary to fly as far as Toledo, Ohio before turning around and coming in at the time stated. Had it come in when first cleared it would be landing at approximately the right time to be Flight UAL 93.
It would have been possible to have passengers of either UAL 93 (from Newark) or UAL 175 (from Boston) to have boarded Delta equipment, thanks to a prior arrangement with the airlines involved. United and Delta have a history of cooperation and there may be some overlap in the respective boards of directors. A quick briefing with the pilots before takeoff might well result in an announcement such as the following:
“Ladies and gentlemen, you have probably noticed by now that we have boarded an aircraft from Delta Airlines. This is what we call a ‘loaner.’ The plane we were going to use had a malfunction in one of the main gears, so Delta kindly let us use the present equipment. Let’s have a hand for Delta.†(sound of scattered clapping)
This scenario does no commit itself to such a switching operation, but includes it as a possibility in order to make the Cleveland landings of Delta equipment more credible. In any event the Cleveland airport had been cleared by the time of the landings, so it may not have made any difference what livery the landing aircraft carried.
After takeoff and climb out, Flight 93 was hijacked at approximately 9:30, some 50 minutes after takeoff and climb out. We assume that the hijacking method employed for Flight AAL 77 was probably used in this case, as well. At that point the passenger aircraft was carrying the transponder code for UAL 93, even as the A-10 shadow aircraft flying nearby carried the code for DAL 1989. In the course of the hijacking operation, the A-10 carried out the radar swap, changing its code to UAL 93, even as that aircraft took up the DAL code previously used by the shadow aircraft. A few minutes after changing course toward the south, the shadow aircraft turns off its transponder, having already convinced TRACON personnel that it was Flight UAL 93.
We will now examine events in the flight of UAL 93 from the perspective of the ATC controller handling Flight UAL 93. The scenario will be matched to a
37
transcript of the actual radio traffic between a controller at the Cleveland ATC (“Cleveland Centerâ€) and a number of aircraft flying through his sector. (Vialls 06) We have seen various excerpts of this transcript in the media, but they rarely agree with each other — or the one that appears here — in certain particulars regarding suspicious transmissions.
Note that pilots calling in always announce their presence with their flight number. Conversely, the controller always addresses them by flight number so there is no confusion about which pilot a given instruction is meant for:
Cleveland: United ninety-three, check in when flight level three-five- zero – [unintelligible].
United 93: United ninety-three. Check in three-five-zero.
Cleveland: United ninety-three, three-five-zero, Roger. United ninety-three, you have traffic to your one o’clock, twelve miles eastbound three-seven-zero.
United 93: Negative contact. We’re looking. United ninety-three.
Up to this point, everything appears to be going well, with UAL 93 confirming the instruction to ascend. Then Cleveland warns UAL 93 that another aircraft, currently 12 miles away, is coming toward it at an altitude of 37,000 feet (about 2000 feet higher than the assigned altitude for UAL 93). Flight 93 confirms the message by saying, “We’re looking.†Such warnings are routine whenever the (horizontal) separation of aircraft falls below a certain minimum distance.
Cleveland: Somebody call Cleveland? (What the operator heard is not recorded on this tape, but may have come in at a different frequency.) United ninety-three, verify three-five-zero. United ninety-three, verify your flight level, uh, three-five-zero. United ninety-three, verify your flight level is three-five-zero. United ninety-three, Cleveland. United ninety-three, Cleveland. United ninety-three, do you read Cleveland Center, please?
Somebody in Cleveland Center has just heard something peculiar on another frequency and has informed this particular controller. It has to do with Flight UAL 93. The controller for UAL 93 evidently has a concern about the aircraft’s
38
altitude, asking the pilot to confirm his altitude. At this point the UAL 93 transponder code may have disappeared from the controller’s screen (along with the altitude number). This would explain why the controller feels he must get voice confirmation of the aircraft’s altitude.
United 797: United fifteen twenty-three, did you hear the company, uh, did you hear some other aircraft on a frequency a couple of minutes ago, screaming?
United 1523: Yes I did, Seven ninety-seven. And, uh, we couldn’t tell what it was either.
United 797: Okay.
Two of the other aircraft in this controller’s sector briefly discuss the strange noises they have heard. Meanwhile, the controller must now keep an eagle eye on Flight UAL 93. Its flight path has deviated from the planned route and it no longer shows its transponder code or altitude.
Cleveland: United ninety-three, Cleveland. If you hear the center, ident. (Flight 93’s transponder has evidently been turned off. The “ident†instruction is a request to turn the transponder on.)
The time is now a few minutes after 9:40 am, when Flight 93’s transponder has gone off. Shortly after Cleveland asks Flight UAL 93 to turn its transponder back on, two other pilots (AAL 1060 and EXEC 956) call in about the previous noises. Next, they will all hear a new transmission in which someone who is not the captain of Flight UAL 93 goes on the air as a hijacker, complete with overdone accent and a message to passengers â€accidentally†keyed to the radio transmitter. It should be added, for the sake of continuity, that as these events develop, the controller has his eyes fixed on the naked blip that was Flight 93 before its transponder went off. But he must look away frequently to judge the position of each aircraft in his sector, including a quick assessment of potential hazards to each,
United 93: . . . this is captain. Please sit down. Remain sitting. We have a bomb on board.
Cleveland: Uh, calling Cleveland Center, you’re unreadable. Say again
39
slowly.
Executive 956: [unintelligible] sounded like he said he had a bomb on board.
Cleveland: Uh, say again. You there, United ninety-three?
Executive 956: . . . was reasonable, sounded like someone said they had a bomb on board.
At this point, the Cleveland controller sees Flight 93 (in reality the shadow aircraft) turning south and calls DAL 1989 to warn it of the errant aircraft.
DAL 1989 (i.e., UAL 175) never gets a chance to respond. Another mysterious message breaks into the frequency in timely fashion.
United 93: . . . this is the captain. We have a bomb on board [unintelligible] – I am going back to the airport, they have met our demands [unintelligible].
This transmission is the probable source of the story that Flight DAL 1989 had a bomb on board. It involves the same strange voice, this time saying, “They have met our demands.†The voice, intended to imitate what a hijacker might say, declares that since the “demands†have been met, he will now take the plane back to the airport. In the context of 9/11, this transmission makes no sense, unless it is a war-games exercise following an unknown story-line.
The tape ends shortly after this. The last known heading of what the controller thinks is Flight UAL 93 was roughly in the direction of Washington and later it will be “evident†that this is the flight that crashed at Shanksville on its way to either to the White House or the Capitol building.
Flight UAL 93, which the controller thinks is DAL 1989, continues on its westward heading. Owing to the possibility that the mysterious transmission came from DAL 1989, Hopkins airport is thoroughly evacuated and DAL 1989 comes in for a landing at 10:10 am. Not only the terminal is evacuated, but the NASA Center and the FAA building, as well. (WB 2004) Only essential personnel remain at their posts. The evacuation, ostensibly carried out as a safety measure, is actually a witness-clearing operation.
40
Passengers are reportedly confined to the “DAL 1989†aircraft until 12:30 pm, when officials begin evacuating it. Some 69 passengers are reported to be aboard the aircraft. Even if this figure is fictitious, it’s close to the number of passengers aboard UAL 93. The passengers are evacuated to the (now vacant) FAA building and the aircraft sits on the runway near the I-X Center for some time after this, there being no record of an immediate takeoff. It may have remained in that position until the general flight ban was lifted later in the day.
In this scenario, both former UAL/DAL aircraft are later flown by specially designated pilots to the Davis-Monthan airbase in Arizona, an air force scrap yard and mothballing operation, with an immense acreage and many secluded areas. In one of these areas, the aircraft are given an acid scrub and cut up for scrap, with steel, aluminum, and titanium parts being sent out for recycling.
Once again, any of the genuine passengers on Flight 93 would have been taken care of as in the previous cases. It may have been part of the original plan to have “Flight 93†crash precisely where it did. The point had already been made by the other strikes and the crash in Shanksville was to become the basis of the heroic story of Todd Beamer.
4.2.4 Flight UAL 175
According to the official story, Flight UAL 175 was a Boeing 767 carrying 56 passengers and nine crew members. It departed Boston’s Logan airport at 8:14 am and flew uneventfully west until, at 8:40 am, it’s transponder was turned off. Two minutes later, it began to veer to the south. This is the plane that was alleged to have struck the south tower of the World Trade Center at 9:02 am
The plane that actually struck the south tower was not Flight UAL 175, however. Just before striking the tower, it banked abruptly to its left, turning into its target. The effect on the television audience was that of a pilot avoiding a near miss.
Following the north tower impact, the streets around the WTC complex were abuzz with multiple news cameras and scores of New Yorkers on hand with video cameras to capture a piece of history for themselves. Since the plaza area around the north tower had been cleared by police, the only good vantage point for both towers was south and west of the south tower. Thus most witnesses to the crash were on the south side of the incoming aircraft’s flight path. The south tower impact was one of the most heavily filmed events in recent American history. The
41
videotapes all show much the same thing, an almost vertical (straight up) view of the aircraft from various vantage points below it and within a block or two south of the tower. (Liberty Street area) None of these videos show windows on the aircraft, since the aircraft was banked to the left, tilting all the windows (or lack of them) skyward. The many eyewitness statements recorded in the event have the usual variations in detail. The only professional account was given by on-the-spot news reporter Mark Burnback for WCBS/Fox News. (FOX 2001))
If a majority of news cameras were on one side of the incoming aircraft’s flight path, it might well bank away from that side as it came in — if it had no passenger windows. Burnback, however, was on the street to give oral reports of street level activity, unaware that a second aircraft was about to crash into the south tower, and apparently on the “wrong†(north) side of the flight path. He reported what he saw immediately:
"…there was definitely a blue logo, it was like a circular logo on the front of the plane, uh…toward the…uh…towards the front, um… it definitely did not look like a commercial plane, I didn’t see any windows on the sides and [it] definitely was very low… it was not a normal flight that I’ve ever seen at an airport…"
In another video record of the event (IPS 2004), one sees the aircraft cross the sky behind a lady who watches it hit the tower. She then turns to run away (toward the camera), screaming, “It’s not an American Airline! It’s not an American Airline!†From that distance the viewing angle is more horizontal than vertical, but the aircraft would be too far away for windows (or lack of them) to be visible. On the other hand, a complete lack of airliner livery would be visible and we therefore assume that the lady was reacting to this feature.
The incoming aircraft has been positively identified by aviation experts as a Boeing 737 used by the air force in various roles. The engine found on the street just outside the south tower is claimed to be the engine type used in the Boeing 737. (Carlson 2005))
According to our assumptions about the two Delta flights at Cleveland’s Hopkins Airport, Flight 175 was hijacked about half an hour after takeoff and in much the same way as AAL 77 and UAL 93 were hijacked. The radar swap with the military KC 737 took place approximately 100 miles west of New York City. We will assume that the transponder code carried by the shadow aircraft was DAL 89, not a scheduled flight for that day and probably one of the aircraft involved in
42
Amalgam Virgo exercise.
Judging from the rather sharp change in direction attributed to the flight at this point, we will assume an X-swap, with the KC 737 shadow aircraft taking on the transponder code for UAL 175 and, again, carrying it just long enough to catch the attention of TRACON. Thereafter the tanker would be little more than a blip being watched intently by air traffic controllers as it veered toward New York from the south, heading for the WTC south tower.
Meanwhile, the transponder code for DAL 89, previously carried by the shadow aircraft, was taken up by UAL 175, now identifying itself as a Delta flight, one that would soon report a bomb on board.
As it passed south of Cleveland Hopkins, DAL 89 requested permission to land, but was not in a good position to come around when permission was granted. It flew west as far as Toledo before returning and landing at 10:45 am. It then taxiied to an unused strip beside the NASA John Glenn Research Center. Half an hour later, officials of unknown affiliation began moving the passengers into the NASA facility, which was itself evacuated just prior to 10:00 am. Some “200 passengers†were reported to be aboard. Since this was an unscheduled flight, it was almost certainly one of the aircraft used in the war games. This way, its real identity as Flight UAL 175 was successfully masked and senior airport officials would have regarded it as part of the ongoing exercises or the winding-down of same, given the horrendous events of the day. In any event, those handling the plane at its isolated location by the Glenn Research Center were playing out an evacuation exercise with or without real people, as far as those same airport officials are concerned. By now readers are familiar with the methods of human disposal outlined earlier and there is no need to add any further details to this scenario.
4.3 Follow-up: reinforcing the story
Broadly considered, Operation Pearl did not end on September 11, 2001. Downstream from that date it was important to reinforce the official story through a variety of special operations that were designed not to check the official story, but to shore it up against growing skepticism.
Thus at various times over the next several months (and years), news stories would surface that, for example, after a massive ID effort 184 of the 189
43
Pentagon victims had been positively identified through their DNA or that two of the hijackers participating in the WTC attacks had been identified through their DNA (CNN 2003). The identification process depended critically on having a tissue match between remnants located on site and samples obtained from victims homes. (toothbrushes, hair combs, etc.)
The intention of this operation was to reinforce the official story by providing such strong corroborating evidence that people believing the story would agree with the general media assessment of 9/11 researchers as cranks and “conspiracy theorists.†After all, is any evidence as powerful as DNA evidence? Of course not, provided that tissue samples actually a) came from passengers and b) the passengers were aboard the aircraft that struck the Pentagon. I add b) because tissue samples could easily have been taken from the dead passengers at Reagan International following the disposal of Flight 77 under the present scenario.
However, why go to the trouble if all you need are tissue matches? Human tissue, after all, is human tissue. Any human being can supply it, even without necessarily dying. Hospitals would be great sources of human tissue — if you know the right people. In any case, while FBI agents might well visit the homes of 9/11 victims to search bathrooms for combs, toothbrushes and other possible sources of tissue, what officials gave to the DNA technicians were paired tissue samples, one of hair follicles and fingernail pairings gleaned from source A, the other of tissue removed from a body B. Given access to human (non-victim) tissue, however, one might arrange that, far from being collected much later (e.g. from the home of a victim), the “gleanings†and the more robust samples are collected from exactly the same source and at the same time. And of course the tissue samples match. The fact that DNA technicians find a match between samples means nothing unless those same technicians acted in a forensic capacity from the very beginning, establishing a chain of custody for all tissue samples, instead of merely taking the FBI’s word for it.
Even relatively minor aspects of the story would be reinforced. Although the mysterious landings at Cleveland received mainly local coverage, it would be important to reinforce the impression that DAL 1989 and DAL 89 had nothing to do with Flights UAL 175 and UAL 93. Hence the following account by a “passenger.†(Anon 2001)
The statement is anonymous and from the personal point of view of a female employee of a company (anonymous) that had arranged for some eight of its
44
employees (all anonymous) to fly to the west coast on another flight. The woman refers to her husband (anonymous) and her children (anonymous), as well. She describes a long wait aboard the aircraft prior to deplaning, then the subsequent interview inside the FAA building. The story begins as follows:
“[My spouse] and I and six other fellow […] employees were on the 8 am flight from Boston to Los Angeles on Tuesday, but we were on the Delta flight [1989], the one out of three 8 am flights departing Logan that did not get hijacked. Instead, we were forced to make an emergency landing in Cleveland because there were reports that a bomb or hijacking was taking place on our plane. The pilot had radioed that there was suspicious activity in the cabin since one of the passengers was speaking urgently on his cellphone and ignored repeated flight attendant requests to stop using his cell phone while in flight.â€
The author of this document was apparently unaware that a cellphone would not function at all in a commercial aircraft at altitude. Yet he (or she) has a passenger carrying on a conversation “urgently.†The plane lands and the narrative continues:
“. . . we were all eventually released and went back to the airplane to gather our belongings. We were then escorted out of the airport without going through the main terminal to avoid what the FBI called a "media circus" because the mayor of Cleveland was holding a press conference stating that there was a bomb on our plane and a hijacker in the cabin.â€
The Mayor of Cleveland held his press conference downtown and there was no “media circus†at the airport, which was still evacuated. Also the word “escorted†makes it unnecessary to describe the precise form of transportation used, such as buses. The account is detail-laden, full of personal incident and based on a “scrapbook,†pages of which are reproduced (Anon 2001) to add extra credence to the story. The same source has a statement from the alleged captain of DAL 1989, David Dunlap. The pilot’s account is also detail-laden and takes the form of a “diary.†The author of this piece also mentions the cellphone call made by a passenger. This, along with the egregious error in the “media circus†location automatically discredits the entire story. (Finally, who keeps scrapbooks and diaries any more?)
The flight crew, apparently, was delivered to a local hotel by “volunteers.â€
45
“We got back out of the aircraft and got our stuff. Then we waited some more for the airport manager to find us rooms (no small accomplishment.) We were driven to the hotel in volunteers’ personal vehicles, as no traffic was allowed near the airport. We had to exit through the FAA building and walk out to a vacant parking lot, where we were picked up in a mini van and a pick-up.â€
Undoubtedly, the account should have read, “ . . . got back out to the aircraft . . .â€, since they were supposed to be in the FAA building and not in the plane at the time. It is unclear why the airport manager would be the one to book hotel rooms. Delta Airlines had more than two hours to make the arrangements. It is also rather odd that “volunteers†would be required to transport the flight crew to their hotel.
Reading both stories consecutively leads to the strange impression that they were written by the same individual, following the same sentence structure, methods of disinformation, and so on. The fact that both stories contain the same disastrous mistake lends additional weight to the interpretation of the Delta flights being UAL 93 and 175.
In addition to these specific reinforcement operations, other “terrorist†acts at Bali, Madrid and elsewhere served to reinforce the 9/11 OCT simply as alleged acts by the same terrorist gang — Al Qaeda. And of course, a continuing stream of faked bin Laden video and audio tapes to maintain high levels of terror.
The (Mainstream) Media
The role of the media in 9/11 and in subsequent actions has puzzled some and angered many. Why have the mainstream media refused even to consider seriously the evidence that the official story of 9/11 was false? Frustrating as the refusal may be, it does not necessarily mean that the media were/are complicit in covering up the true nature of 9/11. Media owners have always dictated editorial policy. It is undoubtedly one of the joys of ownership (especially in an era of declining media revenue). Normally the policy directives are not too draconian, perhaps reflecting a political or some other bias that many people take for granted. How would a media owner dictate that skeptical views of 9/11 must never be aired or published? Could such a directive ever be made to appear innocuous? Of course. Simply generalize the directive in an innocuous direction that every senior-level manager would not find at all questionable:
“There shall be no publication or broadcast that undermines or tends to undermine
46
the War on Terror. Our media outlets will play their patriotic role by getting behind President Bush in his present mission.†etc, etc. This directive would automatically prohibit the airing or publication of skeptical material and the decision not to air or publish would be made by senior editors or publishers on their own.
On the other hand, more direct forms of control would appear to be possible. An unverified file of some 1500 memos released by an unnamed, but “conscience- stricken (media) executive†to Walter Storch at TBR News reveal a pattern of news directives that are highly specific in relation to the Wars in Iraq and Afghanistan, as well as in domestic and European politics. (TBR 2003) These directives, sent to the executive by someone higher up in the news chain go rather further than what we normally understand by the word “propaganda.â€
For example, here is one of the memos giving instructions for the coverage of antiwar demonstrations at home: (March 10) “. . . pro-Government rallies are to be given the fullest coverage . . . if antigovernment demonstrations are shown, it is desired to stress either a very small number of "eccentrics" or shots of social misfits; i.e., with beards, tattoos, physical deformities, etc. Pro-Government supporters should be seen as clean cut with as many well-groomed subjects as possible . . . subjects should stress complete support for the President’s programs and especially support for American military units en route to combat…also interviews with photogenic family members of participating GIs stressing loyalty and affection. American flags are always a good prop in the background . . . “
As for international news coverage, the issuer of the memos is eager that all skeptical war coverage in Europe, particularly France, is to be ignored. In one memo, the following draconian restriction appears: “(Feb 10) …It is not permitted at this point to use or refer to any film clips, stills or articles emanating from any French source whatsoever.â€
And in another, “(April 4) . . . a discussion of French desecrations of American and British war graves in France is to receive specific notice. Also, damage to the 9/11 memorial in Paris is to be included. No pictures of swastikas or other defamatory and anti-Administration graffiti are to be shown. French official apologies are permitted . . . no comments equating the President with Hitler will be made . . . and the invasion of Iraq may not be compared with Hitler’s invasion of Poland, and such allegations now being made extensively in offshore media coverage are not to receive any attention. The Iraqi campaign is officially a
47
campaign by a democratic United States against ruthless cruelty and oppression.â€
5. The Checklist revisited
The checklist of anomalous evidence can now be revisited, the anomalies being treated not as unknowns or accidental features of the attacks, but as key ingredients.
The Hijackers: a) not on AA or UA flight manifests b) unable to fly even light aircraft
c) taking westward excursions before turning to targets d) behaving in totally unislamic fashion
The Hijackers did not appear on flight manifests of the day because they were not aboard the aircraft. It doesn’t matter that they were unable to pilot an aircraft (of any description) since they didn’t fly any of the alleged aircraft, in any case. The westward excursions taken by two of the aircraft can be explained in the case of UAL 93 by it’s need to land in Cleveland. Flight AAL 77 flew west for reasons of timing, it being necessary to space the attacks out for more effective media impact. It also reinforced the Cleveland leg of UAL Flight 93 as part of the hijackers’ modus operandi. In the case of “ringleader†Mohammed Atta, there is considerable doubt about his status as a Muslim, although he was almost certainly born into an Islamic family. In addition, Atta was known to have links to the CIA. (LW 2011)
Air force inaction
Air force inaction was absolutely necessary for the attacks to succeed. Fighter pilots would not be privy to the dark side of the war-games taking place on September 11 and would report some strange sights, including two noncommercial aircraft heading toward New York, as well an A10 Thunderbolt closing on Shanksville.
Transponders turned off
Transponders were turned off to make the radar swaps workable. Without radar swaps, the ruse would have been immediately obvious to all ATC personnel.
Destruction of WTC buildings 1, 2, and 7
48
WTC buildings 1 and 2 had to be destroyed completely, not only to amplify the drama of the day, but to hide evidence pointing to the true nature of the attacks. The actual identity of the incoming aircraft, including a complete lack of passengers, would be effectively concealed in a pile of debris that contained millions of tons of concrete, steel, office furniture, mangled body parts of office workers, and so on. It is unclear at this time why WTC Building 7 was demolished.
Absence of significant debris: a) at the Pentagon b) at Shanksville PA
Significant debris was absent from the Pentagon and Shanksville crash sites for the simple reason that no commercial jetliners crashed at either location. The debris is more consistent with a cruise missile.
Impossibility of high-altitude cellphone calls
No cellphone calls were placed at any time from any of the hijacked aircraft for the simple reason that no one aboard thought they were being hijacked. The cellphone calls would not have succeeded, in any case. However, the calls were a key ingredient in the cover story of 19 Arab/Muslim fanatic boogeymen doing the deed.
6. Conclusions
Given the many problems with the official scenario as an explanation of the events of September 11, 2001, we have tried to construct a scenario that accords with the facts on the ground. We do not claim that it is accurate in all respects. Indeed, that would be highly unlikely, given the many gaps that remain in available information. However, we expect that something very similar took place on that day.
Viewing the evidence as a whole and comparing it both to the official story and to the scenario just described, it would be difficult for any sane, rational person (relatively immune to media spin) to accept the official story as a reasonable interpretation of the “terror attacks.â€
Indeed, the deceptions are all rather clumsy and in some cases ill-conceived,
49
considered as operations. The stage machinery interferes with the magic so frequently, one would think that the ultimate perpetrators of this public crime wanted us to be aware, at some point, that the attacks were faked. We must therefore be no less wary of the success of our investigation than of its failure.
Summary of “hijackingsâ€
Flight
AAL 11 UAL 175 AAL 77 UAL 93
swap type
at start (Logan) gate en route X at end (Pentagon) I en route I
substitute
smaller aircraft 737 tanker Skywarrior/Global Hawk A10 Thunderbolt
Acknowledgments
The author acknowledges with profound gratitude the assistance of Panel members Derrick Grimmer, Jerry Longspaugh, Brad Mayeaux, George Nelson, and Helen Stace. I also thank Stephen St. John, Richard Stanley, and Gregory Zeigler for their assistance in the preparation of this article.
References
(911 Rev 2005) The 911 Encyclopedia http://911review.org/inn.globalfreepress/lost_terror_drills_11b.html
(Anderson 2001) R. Anderson. Air Defenses Stood Down on 911 After ATC Alerts Given, Rense.Com, Dec 23/01. http://www.prisonplanet.com/air_defenses_stood_down_on_911_after_atc_alerts_ given.htm
(Anon 2001) Anonymous. 2001. Traveling on Delta Flight 1989 on 9/11. Gray Watson Personal Thoughts. http://256.com/gray/thoughts/2001/20010912/delta_flight_1989_9_11/travel.shtml
(Bamford 2001) James Bamford. Body of Secrets. Doubleday 2001. see also http://www.randomhouse.com/features/bamford/author.html
(BFN 2004) Break for News, 2004. Mohamed Atta loved pork chops . . .
50
http://www.breakfornews.com/Mohammed-Atta.htm
(Bollyn 2006) Christopher Bollyn. 9/11 Pentagon eyewitness describes having seen Global Hawk. Rumor Mill News, July 17 2006. http://www.rumormillnews.com/cgi-bin/archive.cgi/noframes/read/90745
(WB 2004) W. Box. The Cleveland Airport Mystery. 9-11 Visibility Project, INN World Report. http://911review.org/inn.globalfreepress/Cleveland_Airport_Mystery.html
(Brown 2008) Christopher A. Brown. Twin Tower Deception and Demolition (Part I) http://video.google.com/videoplay?docid=-6240504594075547308 (Part II) http://video.google.com/videoplay?docid=-5255701680091399090 website: http://algoxy.com/psych/9-11scenario.html
(Carlson 2005) Jon Cartlson. 2005. The rest of the 911 street engine story. Rense.com: http://www.rense.com/general64/wth.htm (CBS 2001) Focus on Florida, CBS News, September 14 2001. http://www.cbsnews.com/stories/2001/09/14/national/main311268.shtml
(CNN 2001) War Against Terror. CNN 2001. http://www.cnn.com/SPECIALS/2001/trade.center/victims/AA11.victims.html
(CR 2005) Cooperative Research. 2005. Reports: July-December 2000 and Feb- April 2001. http://www.cooperativeresearch.org/context.jsp?item=a1105bohringer
(Dewdney 2004) Project Achilles: Cellphone Experiments in a Light Aircraft. Physics 911, May 2004. http://www.physics-911.com/projectachilles
(Dewdney 2005) Islam Does not Support Suicide Attacks. Physics 911, April 2005. http://www.physics-911.com/islamnotsuicidal
(Dewdney 2005) A. K. Dewdney, Operation Pearl, http://www.physics911.ca (archives)
(Dewdney & Longspaugh 2004) The Missing Wings. A. K. Dewdney & Jerry Longspaugh. Physics 911, October 2004. http://www.physics-911.com/missingwings/
51
(FBI 2001) Press Release. 2001. Federal Bureau of Investigation, Washington. http://www.fbi.gov/pressrel/pressrel01/091401hj.htm
(FME 2005) The 9/11 operation: A Summary (Writings of a Finnish Military Expert) http://www.saunalahti.fi/wtc2001/soldier1.htm
(Fox 2001) Mark Burnback reports a non-commercial aircradt striking the soth tower of the WTC. Fox News Sept 11 2001. http://www.youtube.com/watch?v=lYUs9u1YwV0
(Monaghan 2007) Aldan Monaghan. 2007. Flight School Head Admits Neither He nor 9/11 Hijackers Could Fly 9/11 Planes. Google Videos. http://video.google.com/videoplay?docid=6657344134661842874&hl=en
(Gaffney 2009) Mark H. Gaffney, Hanjour, alleged attack pilot of AAL 77. Global Research, July 9 2009. http://www.globalresearch.ca/index.php?context=va&aid=14290
(Goldstein 2001) Amy Goldstein, Lena H. Sun, George Lardner, Jr., Hanjour an Unlikely Terrorist, Cape Cod Times, October 21 2001. http://www.whatreallyhappened.com/hanjour_history.html
(Griffin 2005) David Ray Griffin. The 9/11 Commission Report: A 571-page Lie. May 22 2005 at 911Truth.org: http://www.911truth.org/article.php?story=20050523112738404
(Griffin 2007) Debunking 9/11 Debunking. Olive Branch Press. Northampton MA. 2007.
(GS 2005) Davis-Monthan AFB, Arizona. Global Security http://www.globalsecurity.org/military/facility/davis-monthan.htm
(Harrit, 2010) Niels H. Harrit, Jeffrey Farrer, Stephen E. Jones, Kevin R. Ryan, Frank Legge, Daniel Farnsworth, Gregg Roberts, James R. Gourley, and Bradley R. Larsen. Active thermitic material discovered in dust from the 9/11 World Trade Center Catastrophe. Physics 911: https://physics-911.com/active-thermitic- material-discovered-in-dust-from-the-911-world-trade-center-catastrophe/
52
(IPS 2004) Dave vonKleist. 2004. In Plane Sight (video) http://video.google.com/videoplay?docid=2361717427531377078
(Jacobs 2006) Don Jacobs. The Military Drills on 9-11: Bizarre Coincidence†or Something Else? Physics 911. from The Hidden History of 9-11-2001 in Research in Political Economy series, Elsevier Ltd. 2006. http://www.physics-911.com/pdf/jacobs.pdf
(Jones 2001) C. Jones. 2001. Post at Free Republic. http://www.freerepublic.com/focus/fr/520262/posts
(Jones et al.2009) Stephen E. Jones, Jeffrey Farrer, Gregory S.Jenkins, Frank Legge, James Gourley, Kevin Ryan, Daniel Farnsworth, asnd Crockett Grabbe. 2009. Extremely high temperatures during the World Trade Center destruction. Journal of 911 Studies: http://www.journalof911studies.com/articles/WTCHighTemp2.pdf
(Jones, A 2005) Alex Jones. Mineta testimony on Cheney stand down/shoot down censored. Prison Planet, July 27 2005. http://www.prisonplanet.com/articles/july2005/270705testimonycensored.htm
(LW 2011) Mohammed Atta — the CIA trained asset. Looseword. http://looseword.wordpress.com/2011/09/11/everything-you-never-knew-about- mohammed-atta-the-cia-trained-asset/
(Marshall, 2006) Andrew Marshall. A Rebuttal to a Rebuttal. The Peak, Simon Frazer University October 30 2006. http://www.peak.sfu.ca/the-peak/2006- 3/issue9/le-tin.html
(McChord, 2003) A-10 Thunderbolt. McChord Air Museum. Retrieved from <http://www.mcchordairmuseum.org/ REV%20B%20MAM%20 COLLECTION%20a-10%20%20BORDER.htm>
(McElwain 2001) We note that all complete quotations of Susan McElwain that used to be available on the web have disappeared. The excerpts appearing in this article are nevertheless accurate; AKD
(MCMN 2002) Daniel Hopsicker. Mohammed Atta & the Venice Flying Circus. April 8, 2002. http://www.madcowprod.com/index23a.html
53
(Monty 2011) Dramatic New 9/11 Tapes: ‘Is This Real World or Exercise?†(audio) Blippit New Magazine, Sept 2011. http://www.blippitt.com/dramatic-new- 911-tapes-is-this-real-world-or-exercise-audio/
(Mitchell 2007) Edward Mitchell, Steel Ignores Jet Fuel http://www.physics-911.com/mitchell
(Muga 2010) Ted Muga, Pilot’s 9/11 Position, Ventura County Star, Spetember 20, 2010. http://www.vcstar.com/news/2010/sep/20/pilots-911- position/#ixzz10BeBYCn5
(NatComm 2004) The 9/11 Commission Report. National Commission on Terrorist Attacks Upon the United states. july 22 2004. Norton, New York. 2005. See also http://www.gpoaccess.gov/911/
(NIST 2005) [quoted in] New Study Props up Official 9/11 Conspiracy Theor. Prison Planet. 2007. http://www.prisonplanet.com/articles/june2007/200607animation.htm
(Noble 2001) Stephen O. Noble. 2001. 9/11 Stories. http://www.vanadia.com/nycstories/911stories/stephen_o_noble/
(North 2001) Gary North. The Perplexing Puzzle of the Published Passenger Lists. Rense.Com, Nov 13 2001. http://www.rense.com/general15/perplexingpuzzle.htm
(NYCA 2007) “New York City Activist.†More About the FAA, NORAD, and Intercepts. WordPres.com, Nov 5 2007. http://activistnyc.wordpress.com/2007/11/05/more-about-the-faa-norad-and- intercepts/
(Omholt 2004) 9-11 and the Impossible Pentagon. Ralph Omholt. Physics 911, November 2004. http://www.physics-911.com/omholt
(PQ9 2007) Patriots Question 9/11: http://patriotsquestion911.com/
(Rivero n. d.) Hani Hanjour: 9/11 Pilot Extraordinaire, Mike Rivero, nd. (Spencer 2003) The Incredible 9-11 Evidence We’ve All Been Overlooking.
54
Leonard Spencer. Serendipity. http://www.serendipity.li/wot/aa11.html
(Salavador 29002) Robert Salvador. 2002. World Trade Center Task Force Inteview. http://www.checktheevidence.com/911/NYT9- 11AccountsAnalysis/txt/9110474.txt
(Schwarz 2005) Karl B. Schwarz. 2005. Special Report, Physics 911. https://physics-911.com/pdf/schwarz.pdf
(Spencer 2005) http://www.serendipity.li/wot/aa11.html
(SPC 2000) FTS Flight termination system. 2000. System Planning Corporation, Langley, VA. Retrieved from www.sysplan.com May 17 2003. See www.sysplan.com/Radar/FTS (flight termination system) and also www.sysplan.com/Radar/CTS (command transmitter system)
(TBR 2003) Controlling the News. (undated material) TBR News. Washington, USA http://tbrnews.org/Archives/a280.htm
(UF93 2001) United Flight 93 Crash Theory Home Page. 2001. How did Flight 93 Crash? Retrieved from <www.flight93crash.com/> June 10, 2003.
(USA Today 2001) USA Today. 2001. Weapons of destruction. www.usatoday.com/graphics/news/gra/gflightpath2/frame.htm (See also (Valentine 2007) below.)
(USAF 98) Global Hawk: U. S. Airforce Fact Sheet. Global Hawk. Aeronautical Systems Center. USAF Langley, VA. Retrieved July 4 2003 from <http://www.af. mil/news/factsheets/global.html>
(USAF 2003) RQ-1 Predator unmanned aerial vehicle. United States Air Force Fact Sheet. Aeronautical Systems Center, USAF, Langley, VA. No date on document. Retrieved from www.af.mil/news/factsheets/RQ_1_Predator_Unmanned_Aerial.
html, May 18 2003.
(Valentine 2007) Carol Valentine @ Public Action: http://www.public- action.com/911/4flights.html
55
(WK-T 2008) (Wikki) http://en.wikipedia.org/wiki/Transponder_(aviation)
(WK-WTC, 2008) World Trade Center, 2008. Wikipedia. http://en.wikipedia.org/wiki/World_Trade_Center
(WRH 2007) http://www.whatreallyhappened.com/hijackers.html
Note: This article is under copyright protection and cannot be reproduced or reprinted without permission of the author.
56
 List of Members
Log in
List of Members
Log in